SNYK로 Djang를 진단해보겠다.

Django를 fork한 후 저장소 주소를 입력해주자.
진단 결과가 나왔는데

분석을 자세히보면 15개의 높은 위험의 취약점이 발견되었다.
높은 위험의 취약점 15개를 보면
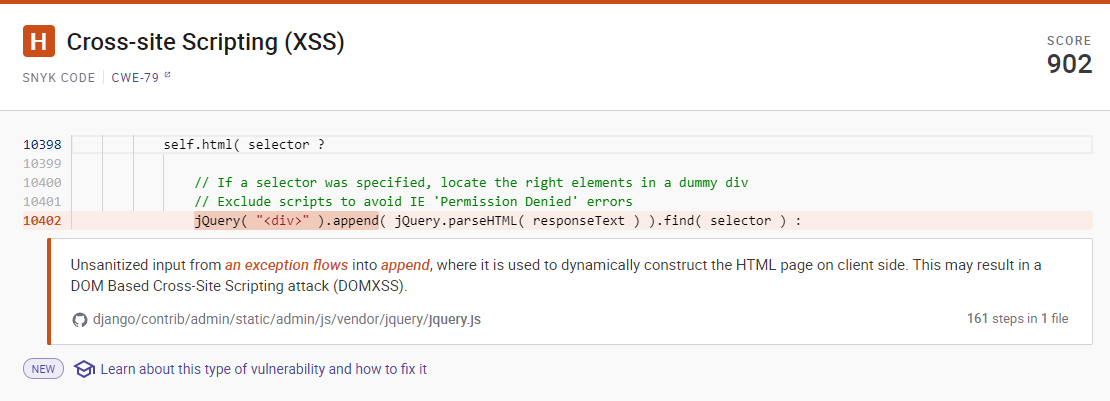




다수의 XSS(Cross-Site Scripting)과 SQL injection이 발견되었다.
https://cwe.mitre.org/data/definitions/79.html
CWE - CWE-79: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') (4.6)
div.collapseblock { display:inline} CWE-79: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')Weakness ID: 79 Abstraction: BaseStructure: SimpleStatus: Stable The software does not neutralize or incorrectly neutralizes use
cwe.mitre.org
https://cwe.mitre.org/data/definitions/89.html
CWE - CWE-89: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') (4.6)
div.collapseblock { display:inline} CWE-89: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection')Weakness ID: 89 Abstraction: BaseStructure: SimpleStatus: Stable The software constructs all or part of an SQL command using ext
cwe.mitre.org
32개의 중간레벨의 취약점은



다수의 Open Redirect와 Use of Hard-coded Credentials,
Arbitrary File Write via Archive Extraction (Tar Slip)가 발견되었다.
Open Redirect는 최근에 공부한 KISA 소프트웨어 개발보안 가이드에 나와있는 취약점이다.

https://cwe.mitre.org/data/definitions/601.html
CWE - CWE-601: URL Redirection to Untrusted Site ('Open Redirect') (4.6)
div.collapseblock { display:inline} CWE-601: URL Redirection to Untrusted Site ('Open Redirect')Weakness ID: 601 Abstraction: BaseStructure: SimpleStatus: Draft A web application accepts a user-controlled input that specifies a link to an external site, an
cwe.mitre.org

low level 취약점에 다수는
Use of Hard-coded Credentials이였다.
Use of Hard-coded Credentials는
소프트웨어 관리자가 구성한 인증을 공격자가 우회할 수 있는 심각한 허점을 만든다.
https://cwe.mitre.org/data/definitions/798.html
CWE - CWE-798: Use of Hard-coded Credentials (4.6)
div.collapseblock { display:inline} CWE-798: Use of Hard-coded CredentialsWeakness ID: 798 Abstraction: BaseStructure: SimpleStatus: Draft The software contains hard-coded credentials, such as a password or cryptographic key, which it uses for its own inbo
cwe.mitre.org
'SUA > 오픈소스 보안' 카테고리의 다른 글
| [SUA] 오픈소스 보안 7주차 (0) | 2021.11.21 |
|---|---|
| [LGTM] Sherlock 분석 (0) | 2021.11.21 |
| [LGTM] Zapproxy 분석 (0) | 2021.11.21 |
| [SonarQube] Selenium, Spark, Spring-boot 진단 (0) | 2021.11.21 |
| [LGTM] kubernetes 분석 (0) | 2021.11.21 |


